CompleteFTP Enterprise MFT supports Two Factor Authentication (2FA) through the use of the Time-based One-Time Password (TOTP) algorithm, which is supported by most authenticator apps (e.g. Google Authenticator, Microsoft Authenticator and FreeOTP). It can be enabled by checking a single checkbox. Once enabled, web users will be required to install the app and activate the site before they can access CompleteFTP via HTTP/HTTPS. 2FA is not currently supported in protocols other than HTTP and HTTPS. It is, however, compatible with all authenticators available in CompleteFTP, such as SAML, Active Directory, external database and custom authenticators.
2FA invokes the security principle of 'Something you know and something have'. The 'something you know' is your password and the 'something you have' is a device that generates One-Time Passwords (OTPs). With CompleteFTP's 2FA, the device is a mobile phone (Android or iPhone) that has a TOTP-compatible authenticator app installed, and the OTPs are 6-digit PINs that change every 30 seconds. The trick is that only the TOTP server and each specific instance of the app know the value of the PIN at any given time, so if the correct PIN is entered then we can trust that the user has the phone on which the app is installed. The PIN synchronization between the server and the phone is done by scanning a QR code that's generated by Google and scanned by the app. Each QR code is unique to the specific logged-in user on the site.
Once 2FA has been enabled by the admin (see below), users will have to go through an additional step after entering their user-name and password before they can enter the site.
The first time users log in after 2FA has been enabled, or after their activation status has been reset by an administrator, they'll be presented with a page showing (1) instructions on how to install an authenticator app on their iPhone or Android phone and (2) a QR code for the site. Once they're up and running with the app they'll need to scan the QR code to register the site. Immediately after they've done this a 6-digit PIN will be displayed inside the app. They must enter this PIN on the web page and click the 'Activate' button. Once they've done this they'll be granted access to the site.
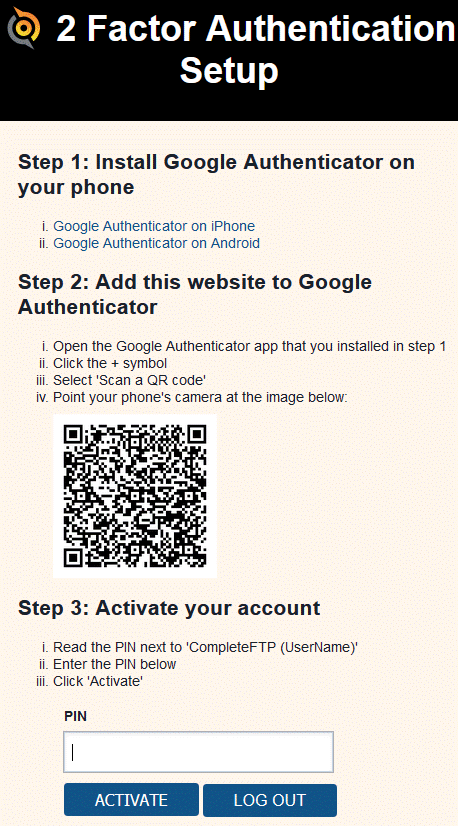
Note that first part of the site identifier, 'CompleteFTP (UserName)', can be modified (see below).
Users can manually activate new devices via the Account Management web-app. This is useful when they've got a new phone.
CompleteFTP's 2FA feature supports backup PINs, which are a set of PINs that don't change with time, but can only be used once each. These are useful for situations where users don't have access to their authenticator app. Backup PINs are generated on demand by the user in the Account Management web-app or by the system administrator in the 2FA status view in CompleteFTP Manager. User can copy the PINs to a safe place, such as a password manager, or obtain them directly from the system administrator.
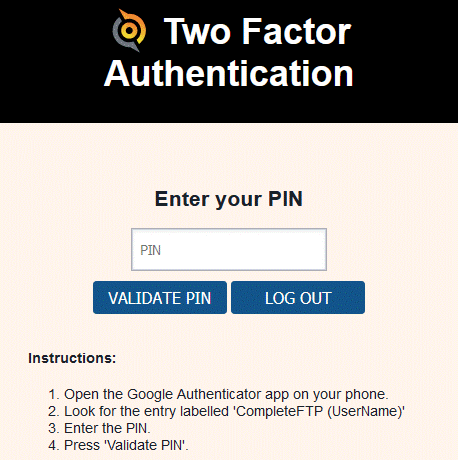
Activation is only required when a user hasn't already activated 2FA. After that they'll only be required to validate by entering the PIN shown in the app.
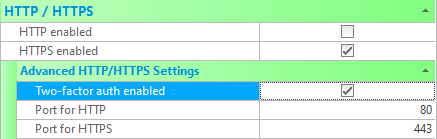
2FA can be enabled in the settings for any site by checking the checkbox labeled 'Two-Factor Authentication enabled'.
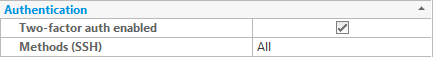
Additionally, the site setting can be overridden for any user by checking or unchecking the checkbox labelled 'Two-Factor auth enabled'.
Users often have multiple sites activated in the authenticator app, so it's important that each site is clearly identified. By default, sites will show up as 'CompleteFTP (username)' in the app, but the first part of this should be customised for the site. It can be changed by setting the Label setting for the site. It should be set to something that identifies the specific site that the user is logging into, such as the name of the organisation, business unit or website.

The backup PINs and activation status of individual users can be managed in the Two Factor Authentication status view, which is accessible from the Users panel in CompleteFTP Manager.
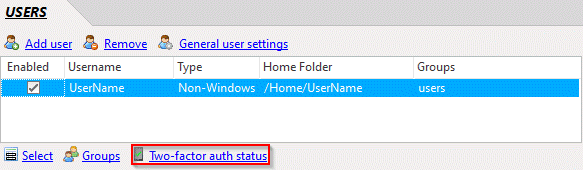
The authentication status view shows the backup PINs and activation status of every user who has used 2FA.
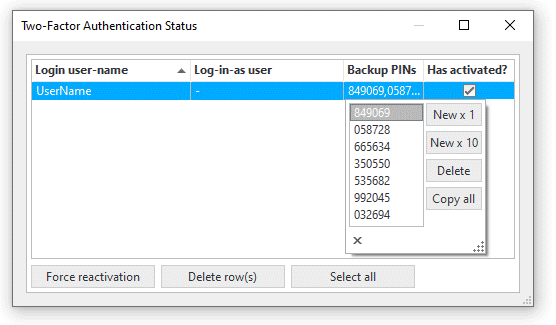
Users can be forced to reactivate by clearing the 'Has activated?' checkboxes one at a time or in bulk by selecting a set of rows and pressing the 'Force reactivation' button. Deleting rows has the same effect, but also clears out backup PINs. Backup PINs can be managed by clicking on a user's 'Backup PINs' field, which pops out an editor for the PINs. PINs can be generated, deleted and copied to the clipboard. Copying to the clipboard enables system administrators to easily send them to users via instant messaging, though it's important that this be done securely. Since the PINs are short they can also simply be read out to the user over the phone, if required.