HTTP/HTTPS is supported in Professional and Enterprise MFT.
The various HTTP/HTTPS settings that are available to configure CompleteFTP sites are described below. Note that settings changes must be saved via the Apply Changes button, otherwise they will be lost.

Please note that HTTP and HTTPS should not be enabled until any other HTTP/HTTPS services on the server machine are shut down, e.g. IIS and Apache. Other products such as Skype also use the HTTP and HTTPS default ports of 80 and 443. If in doubt, use netstat to check what ports are in use. Note that these products can be run simultaneously, but must be configured so their port numbers do not clash. Both Apache and CompleteFTP can be set up with HTTP/S port numbers that differ from the default ports.
There are additional HTTP settings in Limits & Timeouts.
For HTTPS security settings, see the FTP/FTPS Security Settings (as they are shared).
| Setting | Description |
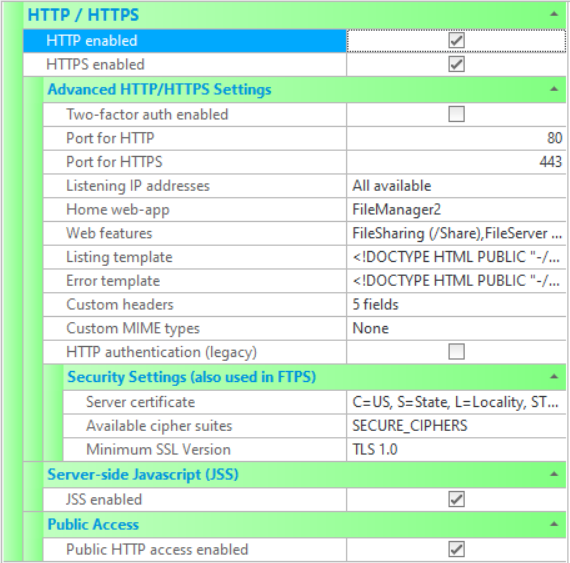
| HTTP Enabled | If checked, the HTTP protocol is enabled. If not checked, HTTP will not be supported by the server. If enabling, ensure that other HTTP servers are not running on the server machine. |
| HTTPS Enabled | If checked, the HTTPS protocol is enabled. If not checked, HTTPS will not be supported by the server. If enabling, ensure that other HTTPS servers are not running on the server machine. |
| Public HTTP access enabled | If checked, unauthenticated users will be able to access any file in the public folder. Unauthenticated users are represented by the user called 'anonymous' (which can be found in Users panel and by selecting "Show system users/folders/sites" in the main form's Options menu). By default the home-folder of this user is /Public, so this is the folder that will be publicly accessible if this option is enabled. |
| JSS enabled | Enable JSS (Javascript Server-Side) for this site. |
| Port for HTTP | Port that is used for HTTP. The standard port number for HTTP is port 80. |
| Port for HTTPS | Port that is used for HTTPS. The standard port number for HTTP is port 443. |
| Listening IP addresses | Lists the IP addresses to listen on for this protocol. All network interfaces can be selected, or individual interfaces selected. |
| Home web-app | Site-default web-app that users will be redirect to after logging in. This is usually the web-based file-manager. This setting may be overridden by the home web-app setting for individual users. |
| Web features | Displays the configured web features. Clicking on the ellipsis (...) will bring up a dialogue box listing each web feature, and showing the configured URL path used by clients to access the application, and whether or not it is enabled. The URL path aan be modified here, and the enabled or disabled status.
By default, Professional and Enterprise MFT support the FileManager1, FileManager2, and FileManager3 features, which allow users to manage files via their browser. FileManager1 is not recommended and is only included for backward compatibility, FileManager2 and FileManager 3 are responsive web-apps that works well both on desktops and mobile devices. FileManager2 is currently the default, but FileManager3 will soon made the default in an upcoming version. Users are recommended to try FileManager3 and use it if it already covers their requirements, as it is more secure. The WebAdmin application provides basic configuration functions through a browser interface: either desktop or mobile. The FileServer application is responsible for serving files via HTTP. If it's disabled, individual files will be unavailable HTTP. The FileSharing feature controls access to shared files via HTTP. The Login and Logout feature controls HTTP user logins and logouts. The CustomCommand feature controls the Custom Command Script feature. The SamlSingleSignOn is required for SAML single-sign-on to work. |
| Listing template | Controls the format in which directory listings are displayed to the user. Directories may be listed by users by entering a URL specifying the path of a directory. The listing is rendered using HTML containing macros, such as %FileName%. Clicking on the ellipsis (...) will bring up a dialog permitting the user to enter their own template. See How to format HTML listings for more information. |
| Error template | Controls the format in which HTTP errors are displayed to the user. The default template uses Javascript to redirect the user to their home folder for 403 errors. Clicking on the ellipsis (...) will bring up a dialog permitting the user to enter their own template. |
| Custom headers | A custom header is a HTTP header field that will be include with every HTTP response. By default, the following headers
are included: Strict-Transport-Security (value=frame-ancestors self), Content-Security-Policy (value=max-age=31536000; includeSubdomains),
X-Frame-Options (value=sameorigin) and X-XSS-Protection (value=value). These may be modified or removed as required, and
any other desired headers may be added
CompleteFTP will automatically generate headers, such as Content-Length, Content-Type, Date, Keep-Alive as required. Content-type is calculated using MIME types (see below). |
| Custom MIME types | A MIME type, or Internet media type, is a two part identifier for file formats. In its most basic form, it defines the type and the subtype for a file extension. For example, HTML files are defined as "text/html". The webserver sends the MIME type to the browser as part of the file being downloaded, and the browser uses the MIME type to decide how best to display the file. An HTML file, with a MIME type of "text/html", will be displayed as a web page. Most common MIME types are included by default in CompleteFTP. Custom MIME types can be added, either as additional file types or to override default MIME types. |
| HTTP authentication (legacy) | If this option is enabled then HTTP logins to CompleteFTP will be handled by the browser (usually via HTTP basic authentication) rather than by the CompleteFTP login page. This is not generally recommended as it can cause problems with logouts. SAML Single Sign-On will not work if this option is enabled. |
| Server certificate | Displays the dialog for controlling the server certificate. A server certificate must be set if FTPS or HTTPS is enabled.
The dialog displays the current certificate's properties, and enables a new self-signed certificate to be generated.
Also, a certificate signing request (CSR) can be created to send to a certificate authority (CA) to obtain a CA certficate. This property is shared with the FTP/FTPS settings. |
| Available cipher suites | This setting controls the cipher suites that can be used. Generally, the default is appropriate unless there are special requirements for a particular algorithm. |
| Minimum SSL version | This setting controls the minimum version of SSL/TLS supported on this site (for both FTPS and HTTPS). The default is TLS 1.0, which means that SSL 3.0 is not supported by default. This ensures that the server is not vulnerable to the security flaws of SSL 3.0. |